1
Background
On July 7, 2022, the Cyberspace Administration of China ("CAC") issued the Measures for the Security Assessment of Cross-border Data Transfer (the "Measures"), which will come into effect on September 1, 2022. With the promulgation and coming into effect of the Measures, China’s security assessment system for cross-border data transfer has been finalized.
Article 37 of the Cybersecurity Law (“CSL”), which came into effect on June 1, 2017, lifts the curtain on the security assessment system for cross-border data transfer in China. Under this system, the operator of critical information infrastructure ("CIIO") shall conduct a security assessment in accordance with the measures jointly developed by the national cyberspace administration authority and the relevant departments of the State Council when it is necessary, due to business needs, to transfer abroad personal information and important data generated or collected during its operation within the territory of China.
The Data Security Law (“DSL”) and the Personal Information Protection Law (“PIPL”), which were released and entered into effect in 2021 in succession, have established and reinforced the important status of the security assessment system for cross-border data transfer. Article 31 of the DSL reiterates the importance of the security assessment system for cross-border data transfer and extends the covered entity from CIIOs under the CSL to CIIOs and other data processors. The PIPL provides three types of mechanisms for cross-border transfer of personal information, among which a more stringent requirement in respect of cross-border transfer of personal information is imposed on CIIOs and personal information processors whose processing of personal information reaches the threshold amount prescribed by the national cyberspace authority.
Building on the legislative foundation of the CSL, the DSL and the PIPL, the release of the Measures attracts extensive attention. The Measures will play a key role in regulating cross-border data transfer, protecting personal information rights and interests, safeguarding national security and social public interests, and promoting the security and free flow of data across borders.
2
Application Scope of the Measures
Article 2 of the Measures provides that "These Measures shall apply to the security assessment of the provision of important data and personal information collected and generated by data processors in the course of their operations within the territory of the People's Republic of China by such data processors to overseas recipients. Where there are other provisions in laws and administrative regulations, such other provisions shall prevail."
Figure 1 Application Scope of the Measures
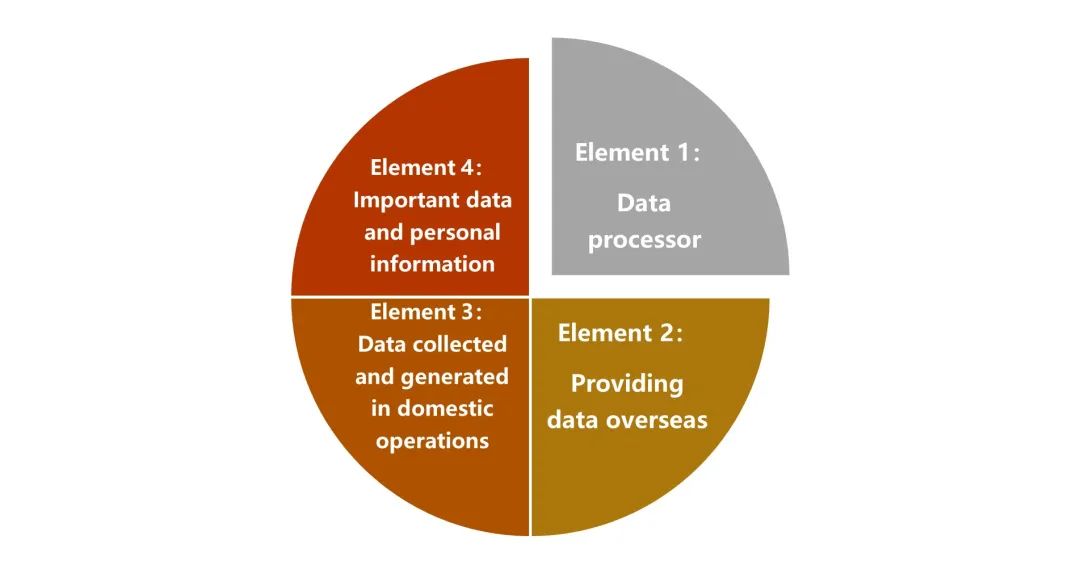
We set out our analysis regarding the above four elements as follows:
(1) Data Processor
The Measures do not define the term "data processor". In fact, neither the DSL nor the PIPL provide the definition of “data processor”. The DSL defines "data" as "any record of information in electronic or other form", and "data processing" as "the collection, storage, use, processing, transmission, provision and disclosure of data". Article 73 of the PIPL defines a "personal information processor" as “any organization or individual that independently determines the purpose and method of processing in their activities of processing of personal information”.
Under the DSL and the PIPL, various administrative regulations and departmental rules have provided different definitions on the term "data processor". We summarize the relevant definitions as follows:
Table 1 Related Definitions on Data Processor | |||
No. | Name | Provision | Characteristic |
1 | PIPL | "Personal information processor" refers to any organization or individual that independently determines the purpose and method of processing in their activities of processing of personal information. | Emphasize the discretion of the processor as to the purpose and method of data processing activities |
2 | Administrative Regulations on Network Data Security (Draft for Comment) | “Data processor” means an individual or organization that independently make decisions on the purpose and manner of processing in data processing activities. | |
3 | Several Provisions on Vehicle Data Security Management (for Trial Implementation) | “Vehicle data processor” refers to organizations that carry out any activity of processing of vehicle data, including automobile manufacturers, parts and software suppliers, dealers, and repair and maintenance providers, car service companies etc. | Based on the whole life cycle of data processing activities, not emphasize the discretion of enterprises as to the purpose and method of data processing activities |
4 | Administrative Measures on Data Security in the Field of Industry and Information Technology (for Trial Implementation) (Draft for Comment) | “Data processors in the field of industry and information technology” refer to industrial enterprises, software and information technology service providers, licensed telecommunications business operators, radio frequency and station users and other entities in the field of industry and information technology, which involve the processing, including collection, storage, use, processing, transmission, provision and disclosure, etc., of data in the field of industry and information technology. | |
Despite the differences in definition, we tend to believe that the term "data processor" in the Measures has the same meaning as that stipulated under the PIPL and the Administrative Regulations on Network Data Security (Draft for Comment), which means that, where an enterprise who was entrusted by a data processor with data processing transfers data overseas, it is the data processor who shall conduct security assessment, and the enterprise the data processor entrusts only needs to cooperate with the data processor as required by the data processor.
The understanding is consistent with the provisions regarding self-security assessment contained in the Information Security Technology - Guidelines for Data Cross-border Transfer Security Assessment (Draft for Comment) ("Assessment Guidelines") published by the National Information Security Standardization Technical Committee ("TC260") in 2017. The Assessment Guidelines provide that if more than one party (in scenarios such as cloud service, subcontract service, etc.) is involved in the cross-border data transfer, the party responsible for the self-security assessment shall be the party who initiates the cross-border data transfer. For example, if a cloud service user requests a cloud service provider to transfer its data abroad, the cloud service provider should cooperate with the user in conducting the self-security assessment and the cloud service user should bear the corresponding liability; however, if the cloud service provider takes the initiative to request transferring the data abroad, the cloud service user should cooperate with the cloud service provider in conducting the self-security assessment and the cloud service provider should bear the corresponding liability. We believe that in the scenario where a cloud service provider requests to transfer the data abroad, it has gone beyond the scope of being entrusted to process the data and is capable of determining the purposes and methods for the cross-border data transfer at its own discretion, and therefore has turned into a "data processor."
(2) Providing Data Overseas
The Measures clarify in the reporter’s Q&As that the cross-border data transfer activities referred to in the Measures mainly include: (i) data processors transferring to and storing data collected or generated in domestic operation overseas; and (ii) where the data collected or generated by a data processor is stored within the territory of China, it can be accessed by overseas institutions, organizations, or individuals.
Except for the abovementioned circumstances, the Assessment Guidelines provide that the provision of personal information and important data to entities which are within the China’s territory but not within the China's jurisdiction or are not registered within China also falls under the scope of cross-border data transfer. In this case, the transfer of important data and personal information to foreign embassies and consulates, foreign aircraft, foreign vessels, etc. which are within the territory of China is included.
In addition, the Assessment Guidelines specify that the following two scenarios will not constitute cross-border data transfer: “personal information and important data not collected or generated in domestic operations are to be transferred abroad through the China's jurisdiction without any modification or processing” and “personal information and important data not collected or generated in domestic operations are to be transferred abroad after being stored or processed within China's jurisdiction and no personal information and important data collected or generated in domestic operations is to be transferred abroad”.
(3) Data Collected and Generated in Domestic Operations
The Measures do not provide further explanation as to the meaning of “data collected or generated in domestic operations". According to the Assessment Guidelines, where a network operator is not registered within the territory of China but carries out business in or provides products or services to the customers in China, it shall be deemed as a domestic operation; however, if a domestic network operator only carries out business or provides products or services for overseas institutions, organizations or individuals, and does not involve personal information and important data of domestic citizens, it shall not be deemed as a domestic operation. Factors to consider when determining whether an entity carries out business in or provides products or services to customers in China include but are not limited to use of Chinese language, use of RMB as the settlement currency, and delivery of logistics to or within China.
(4) Important Data and Personal Information
The PIPL clearly defines the term "personal information" as "any kind of information related to an identified or identifiable natural person as electronically or otherwise recorded, excluding information that has been anonymized."
Although both the CSL and the DSL stipulate that "important data" shall be protected as a priority, neither of them provides a definition for the term. The Administrative Regulations on Network Data Security (Draft for Comment), the Information Security Technology - Rules for Important Data Identification (Draft for Comment), and the Assessment Guidelines have provided for the definition and identification rules of "important data", but they all have not yet been finalized.
The Measures define "important data" as "any data, the tampering, damage, leakage, or illegal acquisition or use of which, if it happens, may endanger national security, the operation of the economy, social stability, public health and security, etc." As the definition in the Measures is still broad, we suggest that enterprises refer to the catalogues of important data issued by various regions, authorities for relevant industries and fields. For example, for important data of the automobile industry, they shall refer to the Several Provisions on Vehicle Data Security Management (for Trial Implementation).
3
Self-risk Assessment and Applying for Security Assessment
The Measures provide for two types of assessment: self-risk assessment and security assessment filed with the cyberspace administration authority, the former one being the pre-condition of the latter one.
(1) Self-risk Assessment
Article 5 of the Measures provides that, a data processor shall, before applying for the security assessment of cross-border data transfer, conduct a self-assessment on the risks in the cross-border data transfer and the self-assessment shall focus on the following matters:
Figure 2 Key Points of Self-risk Assessment

(2) Security Assessment Filed with the Cyberspace Administration Authority
Article 4 of the Measures lists the following circumstances in which the data processor is required to apply for security assessment for the cross-border data transfer with the cyberspace administration authority:
Figure 3 Circumstances Where Data Processor Is Required to Apply for Security Assessment
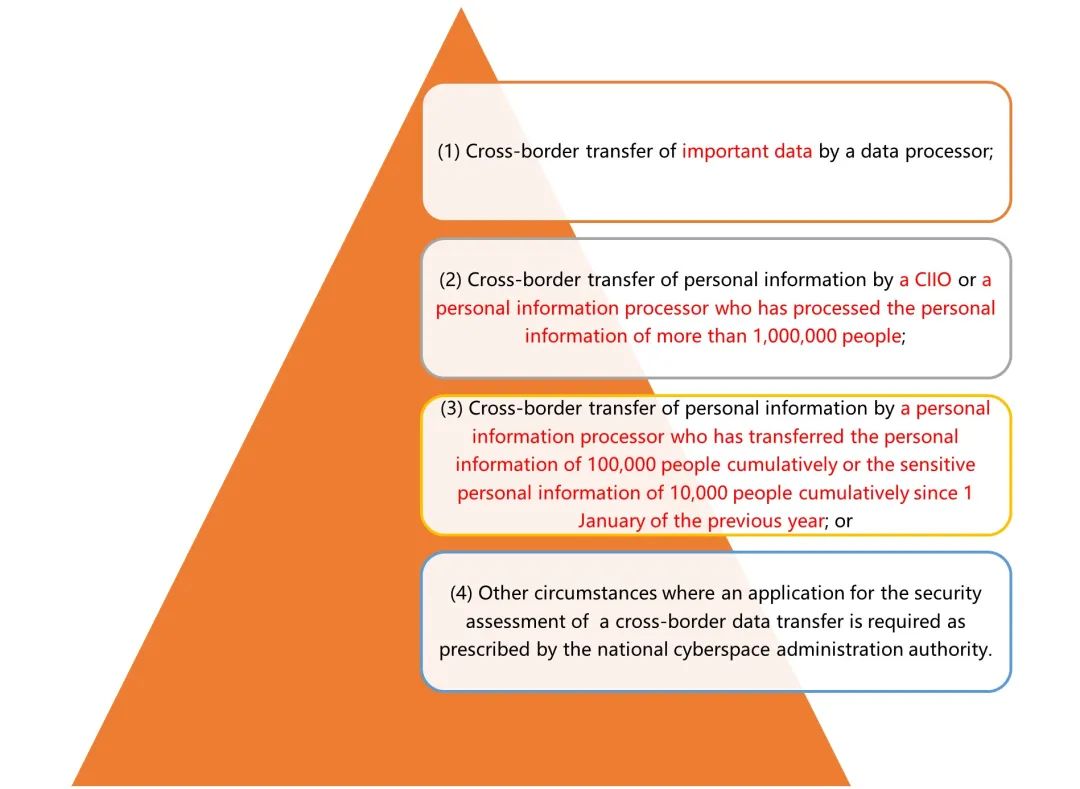
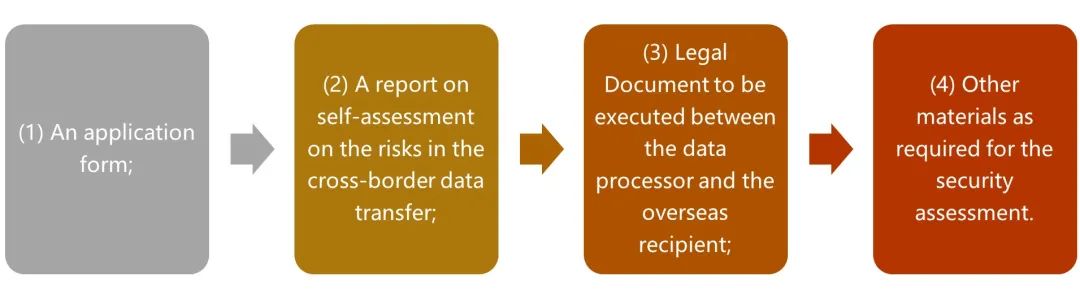
Therefore, before a data processor intends to transfer personal information and/or important data abroad, it shall, in addition to conducting self-assessment on the risk of the cross-border data transfer and producing a report thereof, assess whether the cross-border data transfer will fall under any of the above four circumstances. If it falls under any of the above circumstances, the data processor shall apply for security assessment with the national cyberspace administration authority through the cyberspace administration authority at the local provincial level. Documents to be submitted for security assessment include:
Figure 4 Documents to Be Submitted for Security Assessment
For the cross-border data transfer security assessment, the Measures provide that it shall focus on the risks to national security, public interests, and legal rights and interests of individuals and organizations arising from the cross-border data transfer. By comparing the main items for the security assessment filed with the cyberspace administration authority with the above-mentioned key points in self-risk assessment, we find that, compared with self-risk assessment, the security assessment filed with the cyberspace administration authority places more emphasis on impact of the data security protection policies and legislation and cybersecurity environment of the country or region where the overseas recipient is located on the security of the data to be transferred abroad.
Table 2 Comparison of Key Points in Self-risk Assessment and Security Assessment Filed with Cyberspace Administration Authority | ||
No. | Key Points in Self-risk Assessment | Key Points in Security Assessment Filed with Cyberspace Administration Authority |
1 | (1) Legality, legitimacy, and necessity of the cross-border data transfer and the data processing by the overseas recipient in terms of the purpose, scope, method, etc.; | (1) Legality, legitimacy, and necessity of the cross-border data transfer in terms of the purpose, scope, method, etc.; (6) The compliance with China's laws, administrative regulations and departmental rules; |
2 | (2) Quantity, scope, type, and sensitivity of the data to be transferred abroad, and the risks that may be brought about by the cross-border data transfer to national security, public interests, or the lawful rights and interests of individuals or organizations; | (3) Quantity, scope, type, and sensitivity of the data to be transferred abroad…; |
3 | (3) Responsibilities and obligations undertaken by the overseas recipient and whether the management and technical measures and capabilities of the overseas recipient to perform such responsibilities and obligations can ensure the security of the data to be transferred abroad; | (2) Impact of the data security protection policies and legislation and cybersecurity environment of the country or region where the overseas recipient is located on the security of the data to be transferred abroad; whether the data protection level of the overseas recipient meets the requirements of laws and administrative regulations and the mandatory national standards of the People's Republic of China; |
4 | (4) Risk of the data to be transferred abroad being tampered with, damaged, leaked, lost, relocated or illegally acquired or used during and after the cross-border data transfer, whether the channels for individuals to safeguard their personal information rights and interests are unobstructed, etc.; | (3) … Risk of the data to be transferred abroad being tampered with, damaged, leaked, lost, relocated or illegally acquired or used during and after the cross-border data transfer; |
5 | (4) Whether data security and personal information rights and interests can be sufficiently and effectively ensured; | |
6 | (5) Whether data security protection responsibilities and obligations are sufficiently stipulated in the contract or other documents with legal force to be executed (collectively as the “Legal Document”) with the oversea recipient in relation to the cross-border data transfer; | (5) Whether data security protection responsibilities and obligations are sufficiently stipulated in the Legal Document executed between the data processor and the overseas recipient; |
7 | (6) Other matters that may affect the security of the cross-border data transfer | (7) Other matters to be assessed as deemed necessary by the national cyberspace administration authority. |
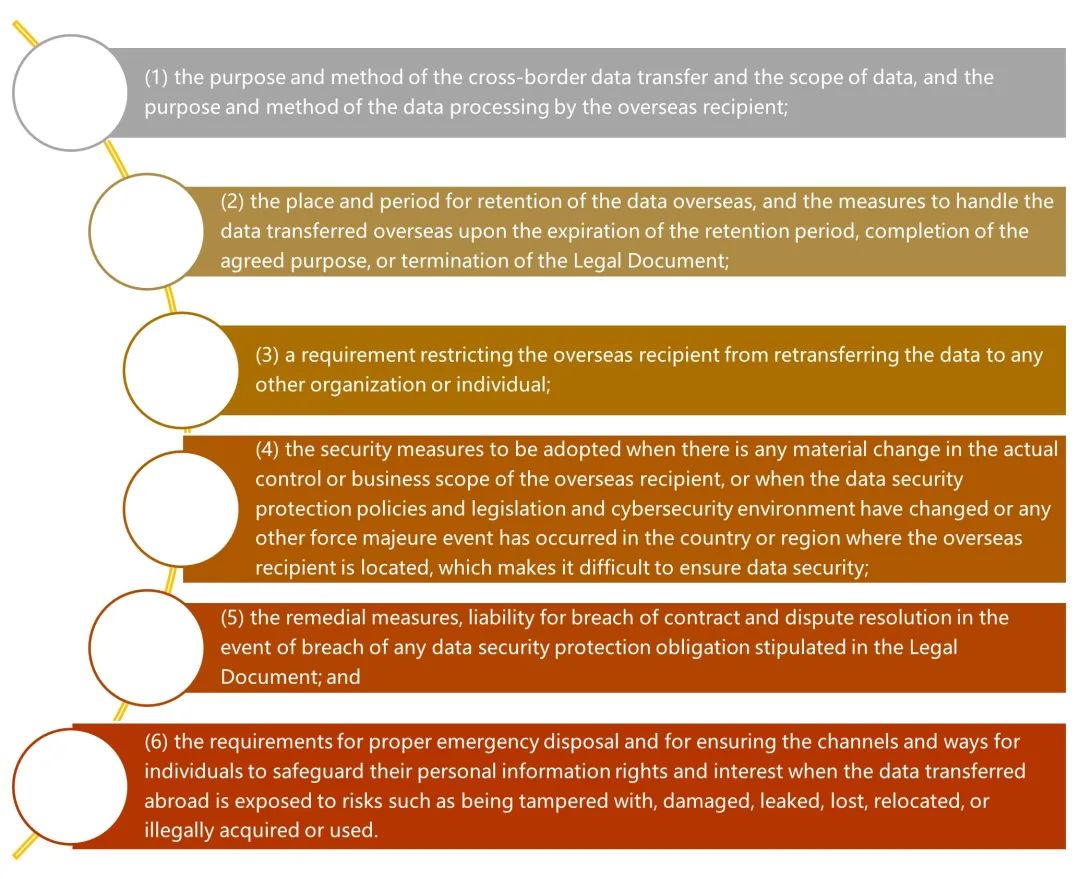
In addition, the Measures provide that the data processor shall expressly agree the duties and obligations of data security protection in the Legal Document to be concluded with the overseas recipient, which shall at least include the following contents:
Figure 5 Main Content of Legal Document
4
Self-risk Assessment and Applying for Security Assessment
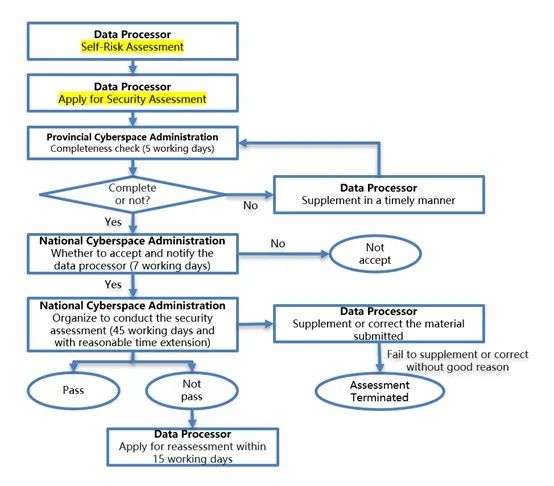
Different from the draft Measures, the Measures provide a layered examination and approval mechanism for the security assessment. The completeness of the application materials will be checked by the cyberspace administrations at the provincial level, and the national cyberspace administration authority will organize the relevant departments of the State Council, the cyberspace administrations at the provincial level and specialized agencies to conduct the detailed security assessment and examination according to the application situations. The specific assessment process is shown below.
Figure 6 Flow Chart of Security Assessment Procedures
The Measures specify that the result of the security assessment will be valid for two years starting from the date on which the assessment result is issued. If the data processor needs to continue to transfer data abroad upon the expiration of the validity period, it shall re-apply for security assessment 60 working days prior to the expiration date.
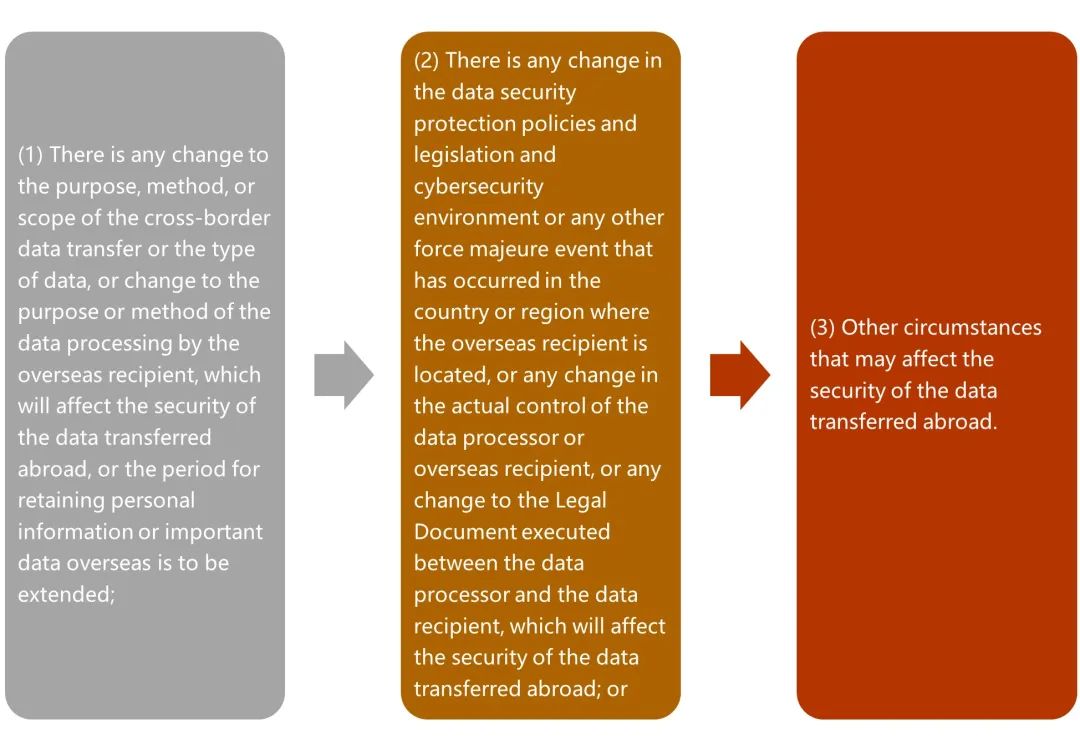
In addition, the data processor shall re-apply for security assessment in the event that any of the following circumstances occurs during the validity period:
Figure 7 Circumstances Where a Re-application for Security Assessment Is Needed
5
Continuous Supervision
The Measures provide that the security assessment for data to be transferred abroad shall be carried out by a combination of ex-ante security assessment and continuous supervision. Therefore, the Measures require that any organization or individual who discovers that any data processor has transferred data abroad in violation of the Measures may report to the cyberspace administration at the provincial level or above.
In addition, in the event that the national cyberspace administration authority finds that any cross-border data transfer activity which has passed the security assessment is no longer in compliance with the security requirements, it shall notify the data processor in writing to terminate the cross-border data transfer. If the data processor needs to continue transferring data abroad, it shall make rectification as required, and re-apply for security assessment after completing the rectification.
6
Recommendations
The Measures specify the obligations of data processors when conducting cross-border transfer of important data and personal information. Therefore, we recommend that enterprises which intend to transfer data abroad carry out a self-assessment in advance according to the type of data to be transferred:
Firstly, attention should be paid to the catalogues of important data formulated by the local authorities in the local region, industry or field. If the data to be transferred abroad is listed in the catalogues, self-risk assessment should be made, and security assessment be applied for in succession in strict accordance with the requirements of the Measures.
Secondly, if the cross-border data transfer only involves personal information without any important data, enterprises need to determine whether it belongs to "a CIIO or a personal information processor who has processed the personal information of more than 1,000,000 people" and whether "it has transferred the personal information of 100,000 people cumulatively or the sensitive personal information of 10,000 people cumulatively since 1 January of the previous year". If yes, the self-risk assessment should be made, and security assessment be applied for in succession in strict accordance with the requirements of the Measures. When determining whether it is a CIIO, attention should be paid to whether the competent departments and regulatory departments of the industry or field in question has issued a relevant notice to the enterprise. In terms of whether it has processed personal information of more than 1 million persons and transferred the personal information of 100,000 people cumulatively or the sensitive personal information of 10,000 people cumulatively since 1 January of the previous year, the enterprise is required to keep record of its data processing activities in its daily compliance work.
Thirdly, it is advisable for a data processor that satisfies the above requirements to file a security assessment for cross-border transfer prior to entering into a cross-border data transfer contract or other legally binding document with the overseas recipient. If the security assessment is to be filed after the execution of the relevant legal document, it is advisable to specify in the legal document that the document shall not become effective until the cross-border data transfer security assessment is passed, in order to avoid any possible losses caused by the failure to pass the security assessment.
Finally, if the enterprise only transfers personal information across borders and it does not constitute a CIIO and the personal information it processes or transfers fails to meet the above thresholds, it is advisable to choose either obtaining the personal information protection certification or signing a standard contract based on the type of the overseas recipient.
In addition, the Measures make it clear that for the cross-border data transfer activities that have been carried out before the effectiveness of the Measures and are not in compliance with the provisions of the Measures, rectification should be completed within six months from the effective date of the Measures (i.e. by March 1, 2023). Therefore, we suggest that such enterprises conduct a supplementary self-assessment against the provisions of the Measures as soon as possible and make rectification if there is a compliance gap and file an assessment timely and accordingly.
Annie Xue


Dr. XUE is a senior counsel (partner level) supervising the compliance practice of GEN Law Firm. She specializes in regulatory affairs in cybersecurity and data protection, antitrust and anti-unfair competition, anti-commercial bribery, and Chinese social credit system. Dr. Xue has extensive experience in the said areas and profound understanding of the complicated issues standing at the intersection of those topics. Dr. Xue studied competition law at the College of Law of the University of Illinois at Urbana Champaign and obtained J.S.D. degree. She also participated in many research topics led by law enforcement authorities and academia as a postdoctoral fellow at the Institute of Law of the Chinese Academy of Social Sciences, and actively contributed to the formulation of competition and data regulatory policies. Before joining GEN, Dr. Xue served as a senior attorney in two Chinese law firms. She authored many articles and reviews related to legal compliance and served as an editor of The China Competition Bulletin hosted by Australia and New Zealand Government College.
CHEN Yang


CHEN Yang focuses on cyber security and data protection, personal information protection and compliance supervision consulting, and has participated in many difficult and complex cases. Yang has the Chinese lawyer qualification and is a Certified Information Privacy Professional (Europe) and Certified Information Privacy Manager by the International Association of Privacy Professionals (IAPP), having rich experience in the field of data protection.
往期文章
中国版SCC发布:《个人信息出境标准合同规定(征求意见稿)》解读(点击可跳转)
《网络安全审查办法(修订草案征求意见稿)》(点击可跳转)
用人单位的合规用工要点——以个人信息保护为角度(上篇)(点击可跳转)
用人单位的合规用工要点——以个人信息保护为角度(下篇)(点击可跳转)
《网络数据安全管理条例(征求意见稿)》附全文(点击可跳转)
《网络数据安全管理条例(征求意见稿)》解读(点击可跳转)
《网络安全审查办法》解读(点击可跳转)
九问九答带您快速了解《智能网联汽车数据安全评估指南(征求意见稿)》(点击可跳转)